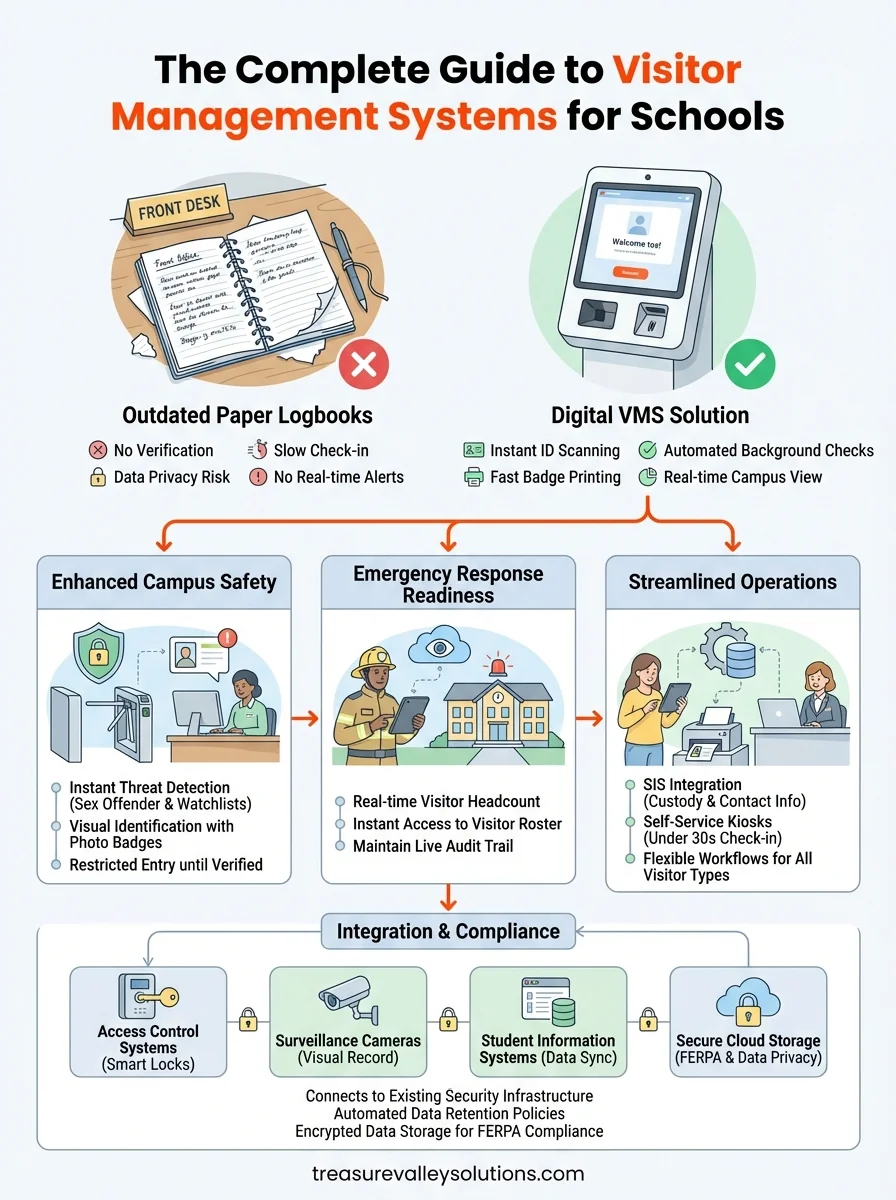
Visitor management systems for schools are digital platforms that automate the entire check-in process when someone enters your campus. These systems replace outdated paper logbooks with instant ID sc...
The Complete Guide to Visitor Management Systems for Schools
Visitor management systems for schools are digital platforms that automate the entire check-in process when someone enters your campus. These systems replace outdated paper logbooks with instant ID scanning, automated background checks, and badge printing that happens in seconds. The technology verifies every guest against national sex offender registries and custom watchlists before they step past the front office. Staff get immediate alerts if someone flagged as a threat attempts to sign in, and administrators can see who's on campus in real time during emergencies.
This guide shows you how these systems protect students and staff while reducing the administrative burden on front office teams. You'll learn how to select the right features for your district, integrate check-in software with existing access control and surveillance systems, and handle data privacy requirements that protect student information. We'll also cover the practical steps to implement a solution that keeps unauthorized visitors out while making legitimate check-ins fast and friction-free for parents, volunteers, and contractors.
Why schools require digital visitor management
Paper sign-in sheets create a false sense of security that puts your students at risk every single day. You have no way to verify whether the name someone writes down matches their actual identity, and you cannot instantly check if that person poses a documented threat to children. The handwritten logbook sitting on your front desk gives you zero protection against sex offenders, individuals with active restraining orders, or non-custodial parents attempting unauthorized pickup. When you rely on this outdated method, your staff spends valuable minutes manually cross-referencing names against watchlists, and those delays can mean the difference between prevention and tragedy.
The limitations of paper logbooks
Your front office team wastes hours each week deciphering illegible handwriting and manually entering visitor data that nobody can search during an emergency. Paper logs create privacy violations because anyone walking past the desk can read the names, times, and purposes of previous visitors. These physical records also deteriorate, get lost, or become unusable evidence if you ever need to investigate an incident or prove compliance during an audit. You cannot generate reports, track patterns, or identify security gaps when your only record is a stack of torn notebook pages in a filing cabinet.

Emergency response requires real-time visibility
First responders need an accurate headcount of every person on your campus within seconds of arriving at an active threat situation. Your paper logbook cannot tell you who checked in but never checked out, which visitors are still in the building, or where those individuals might be located. During a lockdown or evacuation, you need instant access to a complete list of names that updates automatically as people enter and exit. Visitor management systems for schools solve this by maintaining a live roster that you can share with law enforcement from any device, even if the main office becomes inaccessible.
Digital check-in creates an unalterable timestamp and audit trail that paper can never provide.
Instant threat detection protects students
Automated background checks run against national sex offender databases in under three seconds, blocking dangerous individuals before they receive a visitor badge. You can create custom watchlists for specific threats like non-custodial parents involved in custody disputes or former employees banned from campus. The system alerts your staff immediately when someone on these lists attempts to check in, giving you the ability to deny entry and contact authorities before that person moves past the secured entrance.
How visitor management systems improve campus safety
Visitor management systems for schools transform your security posture by creating multiple layers of verification that happen automatically within seconds. These platforms scan identification documents, cross-reference visitor information against threat databases, and produce visual badges that let your staff identify authorized guests instantly. You eliminate the guesswork and human error that comes with manual verification while creating a permanent digital record of every person who enters your campus.
Instant background screening at check-in
The system captures information from a driver's license or government ID using a built-in scanner, then runs that data against national sex offender registries in less than five seconds. You receive immediate alerts if the visitor appears on these databases or matches any custom watchlists you've configured. This automated screening process happens while the visitor stands at the kiosk, giving your staff the ability to deny entry and call authorities before the threat moves deeper into your building.
Visual identification through printed badges
Automated badge printers issue color-coded visitor passes that display the person's photo, name, timestamp, and destination within your school. Your teachers and staff can identify authorized visitors at a glance without stopping every unfamiliar face to ask questions. The system also tracks when visitors fail to check out, sending alerts to your front office if someone remains on campus beyond their expected departure time.
Physical badges create an immediate visual deterrent that discourages unauthorized movement through your campus.
How to choose the right features for your district
You need to evaluate visitor management systems for schools based on how well they integrate with your current infrastructure and adapt to your specific security requirements. The right platform reduces administrative burden while strengthening your ability to control who enters your campus. Focus on solutions that eliminate manual data entry, connect with your existing systems, and handle the variety of visitors your staff encounters daily.
Integration with student information systems
Your visitor management platform should connect directly to your Student Information System to verify custody arrangements and emergency contacts automatically. This integration eliminates the need for front office staff to manually look up student information when a parent arrives for pickup. The system pulls authorized guardian lists from your SIS in real time, flagging any discrepancies or custody restrictions the moment someone checks in. You avoid dangerous situations where a non-custodial parent gains access because your receptionist didn't have immediate visibility into court orders.
Simplified check-in hardware
Deploy self-service kiosks or iPad stations that let visitors complete the entire check-in process without requiring staff intervention for routine entries. Your front office team can focus on monitoring alerts and handling exceptions rather than typing names into a computer every time a parent walks through the door. Choose hardware with built-in ID scanners and badge printers that work reliably in high-traffic environments.

Self-service stations reduce average check-in time from three minutes to under 30 seconds.
Flexible workflows for different visitor types
Configure separate check-in processes for parents, volunteers, contractors, and vendors that match the security level each group requires. Your system should apply different background check thresholds, badge colors, and access permissions based on visitor type. Create workflows that require additional approvals for contractors who need to work near students versus parents attending a quick meeting in the front office.
Integrating check-in software with access control
Your visitor management systems for schools deliver maximum protection when you connect them to your existing access control infrastructure and surveillance cameras. This integration creates automated security workflows that prevent unauthorized entry without requiring constant staff oversight. You transform isolated security tools into a unified system that responds instantly to threats while maintaining a complete audit trail of every person who attempts to access your campus.
Restricting entry until verification completes
Connect your check-in kiosks to electronic door locks that remain secured until the system approves a visitor and prints their badge. You prevent individuals from bypassing the screening process by programming your doors to unlock only after the background check returns clean results. This automated barrier keeps flagged visitors confined to your lobby area where staff can safely deny entry and contact authorities if necessary.
Synchronizing surveillance with visitor records
Link your security cameras to check-in timestamps so you can instantly pull up video footage of any visitor's arrival, movement through campus, or departure. You create visual verification that matches faces to names when investigating incidents or confirming that someone actually left when they claimed to check out. The combined data from cameras and visitor logs gives you complete documentation that paper systems cannot provide.
Integrated systems let you search for a visitor's name and see every camera feed from their entire time on campus.
Professional installation ensures reliable operation
Hire experienced integrators who understand how to connect disparate security platforms through APIs and middleware that maintain system stability. You avoid the compatibility issues and security vulnerabilities that come from attempting to link these tools yourself without proper expertise.
Handling data privacy and compliance concerns
Visitor management systems for schools must protect sensitive information about students and visitors while maintaining records that comply with federal education privacy laws. You handle personally identifiable data every time someone checks in, including government ID numbers, addresses, and the specific students they came to see. Your system needs built-in safeguards that prevent unauthorized access to this information while giving you the ability to produce records when law enforcement or auditors require them.
Meeting FERPA requirements automatically
Your digital platform protects student privacy by restricting access to visitor records based on staff permissions you configure during setup. The system encrypts all data both in storage and during transmission, preventing unauthorized individuals from accessing information about which students receive visitors or who their authorized guardians are. You eliminate the FERPA violations that occur when paper logbooks expose this protected information to anyone walking past your front desk.
Securing data better than paper records
Choose platforms that include automatic data retention policies that delete old visitor records according to your district's requirements without manual intervention. Digital systems create audit trails showing exactly who accessed visitor information and when, giving you accountability that paper logs cannot provide. Your data stays protected in secure cloud servers with redundant backups rather than sitting in filing cabinets where anyone with a key can access years of sensitive records.
Encrypted digital storage protects visitor and student information far better than exposed paper sheets.
Building a safer school environment
Visitor management systems for schools eliminate the dangerous gaps that paper logbooks create while reducing the administrative burden your front office team faces every day. You gain instant threat detection through automated background checks, real-time visibility into everyone on campus during emergencies, and compliance with data privacy requirements that protect student information. The technology transforms your security infrastructure from reactive to proactive by stopping unauthorized individuals before they move past your secured entrance.
Implementation requires careful planning to ensure your system integrates properly with existing access control and surveillance platforms. The right professional partner handles the technical details while training your staff on workflows that match your specific security requirements. Contact our team to discuss how integrated security solutions can protect your students and staff while simplifying daily operations for your district.

